Why Cyber Recovery is of Crucial Importance for Organizations?
 As we are emerging in the technology space and moving into the digital era, one of my primary focuses is to analyze and understand customers’ business challenges, arising threats and difficulties in recovering the data, specifically when their production environment is compromised due to ransomware or a cybercrime. When an organization is compromised to a data breach, data exploitation or data theft is a big threat and protecting the data without data loss and data restoration is the key. Cyber recovery is a emerging trend to identify, categorize and set controls implemented to recover and restore critical systems, data, and operations in the event of a cyber incident or a data breach. It involves strategies, technologies, and procedures aimed at recovering from the effects of a cyber-attack, minimizing downtime, and restoring business continuity.
As we are emerging in the technology space and moving into the digital era, one of my primary focuses is to analyze and understand customers’ business challenges, arising threats and difficulties in recovering the data, specifically when their production environment is compromised due to ransomware or a cybercrime. When an organization is compromised to a data breach, data exploitation or data theft is a big threat and protecting the data without data loss and data restoration is the key. Cyber recovery is a emerging trend to identify, categorize and set controls implemented to recover and restore critical systems, data, and operations in the event of a cyber incident or a data breach. It involves strategies, technologies, and procedures aimed at recovering from the effects of a cyber-attack, minimizing downtime, and restoring business continuity.
As cyber-crimes and incidents continue to evolve and become more sophisticated, organizations must take a comprehensive approach to protect their critical data and systems. While many organizations focus on implementing robust cybersecurity controls, they have started building a solid cyber recovery plan to protect the data and restore the data during an incident.
Cybersecurity Recovery plan main objectives are –

While we all focus on digital transformation in the new normal, the need for strengthening cybersecurity controls and protecting the data has become crucial. Cybersecurity threats are becoming more complex and sophisticated, organizations must take a wholistic approach to protect critical data, assets, and systems. Cyberrecovery is another important control for restoring data after a cyber-attack or a ransomware attack. It is a crucial component of robust cybersecurity to ensure that an organization can recover data after an incident and resume normal operations.
Cyber Recovery planning and enablement protects critical data through five preliminary methods –
- Data integrity, availability, and confidentiality with layers of cyber security controls.
- Cyber recovery planning helps in identifying the risks and in preventing future data loss.
- Isolating the network physically and logically separates the data in a vault.
- Continuous monitoring and taking proactive measures will prevent in becoming victimized.
- Enabling cybersecurity controls in the current threat landscape will help the organization to recover data during an incident.

The Implementation of Cyber Recovery Solution into your data protection environment will enable a defense layer to restore data during an incident. We can also integrate additional technologies and capabilities with your Cyber Recovery environment to increase cyber resilience:
- Implement vault infrastructure and enable data protection layers.
- Enable data backups and build a robust recovery response plan to support Cyber Recovery Vault requirements
- Build and establish a CyberRecovery Vault process to include recovery processes, retention policies, inventory, and applications
- Include training and awareness on the cyber recovery vault to avoid insider threats.
Cyber recovery is emerging in the ecosystem to enhance cyber resilience and to avoid unknown vulnerabilities attacking the surface. Some of the key aspects of cyber recovery and its importance in cybersecurity are:
- Restoration of Data
- Avoid contingency in Operations.
- Protection of Data and Intellectual Property
- Business continuity and Disaster recovery
- Improving Cyber Resilience
- Incident Response Planning
- Legal and Regulatory Requirements
- Identification and Mitigation of Persistent Threats
- Continuous Monitoring
- Applying Proactive measures
Cyber recovery is a crucial aspect of cybersecurity that focuses on rapidly restoring critical systems, data, and operations following a cyber incident or a ransomware attack. It’s not a one day or one time activity to see cyber resilience. It’s enabled by building a robust cyber recovery strategy in place, organizations can minimize downtime, protect sensitive data, maintain business continuity, comply with regulations, enhance incident response capabilities, and continuously improve their cyber resilience. Hence, businesses must be ready with a Cyber Recovery solution to handle the unexpected incidents that’s prone to happen and how an organization will be able to avoid losing the data in the event of a cyber-attack or a ransomware attack.
Cyber Recovery in Action:
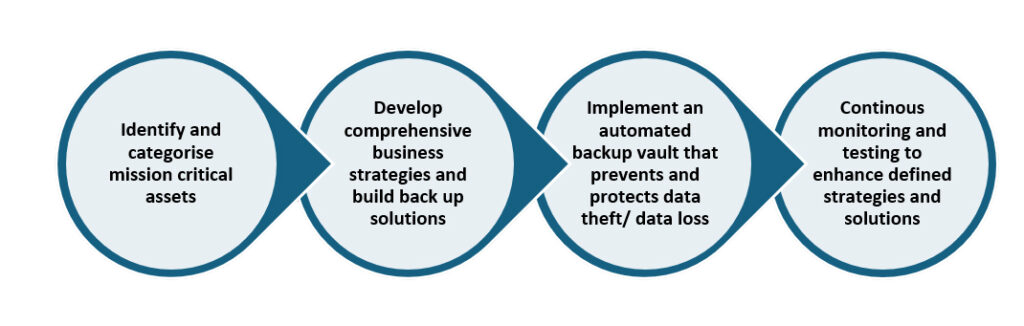
Cyber Recovery planning is built to help organizations protect their critical data and systems from cyber threats and enhance cyber resilience. By implementing the cyber recovery process, it enables protection layers to ensure that critical data remains secure.
Cyber recovery is a crucial component of a robust cybersecurity posture to ensure that the organizations are resilient in nature and how they can quickly recover from cyber-attacks or ransomware attacks during a disruption. Organizations that do not have a solid cyber recovery plan in place are prone to risks of losing data and financial losses during an incident. Hence, its always important that an organization have all of the cyber recovery controls in place to protect the organization from all the known and unknown risks to enhance cyber resilience.
About the Author :

Ms. Kavitha Srinivasulu
Global Head – Cyber Risk & Data Privacy – R&C BFSI
CCISO | DPO | CISM | CEH | CCSO | CCIO| PCSM | PDPP |
Ms. Kavitha Srinivasulu has around 20+ years of experience focused on Cybersecurity, Data Privacy & Business Resilience across BFSI, Financial services, Retail, Manufacturing, Health care, IT Services and Telecom domains. She has demonstrated her core expertise in Risk Advisory, Business Consulting and Delivery assurance with diverse experience across corporate and Strategic Partners.She is a natural leader with versatility to negotiate and influence at all levels.
Ms. Kavitha Srinivasulu is a Board Member of Women in CyberSecurity (WiCyS) India
Ms. Kavitha Srinivasulu is an Executive Committee Member CyberEdBoard Community
Ms. Kavitha Srinivasulu is Bestowed with the following Licenses & Certifications :
https://www.linkedin.com/in/ka
https://www.linkedin.com/in/ka
Ms. Kavitha Srinivasulu can be contacted at :
LinkedIn : https://www.linkedin.com/in/ka
Also read Ms. Kavitha’s earlier article: