When Hackers Employ AI: Is It Time to Rethink our Security Defences ?
When Hackers Employ AI: Is It Time to Rethink our Security Defences?
The rapid expansion of artificial intelligence (AI) across industries has changed countless capabilities, delivering benefits in efficiency, automation, and innovation. However, the same technology has also become a powerful weapon in the hands of predators, essentially altering the landscape of digital threats and malicious activities. As cybercriminals leverage AI to craft more clever and obscure attacks, the level of data protection is questioned. Organisations must relook into their current security strategies to verify, redefine, enhance and remain fit for purpose.
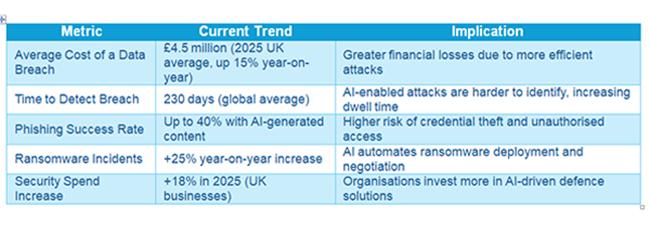
Current Impact on Businesses: Key Metrics
As AI-powered cyber threats rise, businesses are experiencing tangible impacts. Here are some key metrics to illustrate the current landscape:
The Rise of AI-Powered Cyber Threats
Cybercriminals are increasingly leveraging artificial intelligence to enhance both the deception and efficiency of their data exploitation tactics. By implementing machine learning algorithms, these malicious actors can automate activities like credential theft, password cracking, vishing, smishing, and phishing on an unprecedented scale. AI not only accelerates the identification of vulnerabilities within an organization’s systems but also makes breaches and intrusions more challenging to detect and address promptly
 Moreover, the emergence of generative AI has introduced new forms of deception, including highly personalised phishing emails and realistic fake content. These advancements empower cybercriminals to orchestrate multi-layered campaigns that adapt dynamically to security measures, leaving traditional defence mechanisms struggling to keep up. As the tools available to hackers become ever more advanced, the threat landscape continues to evolve at a rapid pace, demanding a fundamental rethinking of how we approach cyber security.
Moreover, the emergence of generative AI has introduced new forms of deception, including highly personalised phishing emails and realistic fake content. These advancements empower cybercriminals to orchestrate multi-layered campaigns that adapt dynamically to security measures, leaving traditional defence mechanisms struggling to keep up. As the tools available to hackers become ever more advanced, the threat landscape continues to evolve at a rapid pace, demanding a fundamental rethinking of how we approach cyber security.
For instance, AI-driven deepfake technology has been utilized to produce highly realistic voice and video impersonations, which are exploited in social engineering attacks. Additionally, automated tools can swiftly scan extensive networks for vulnerabilities, outpacing human capabilities. Furthermore, AI-powered bots can execute coordinated attacks that dynamically adjust to the defences they encounter in real-time.
Risks on using Traditional Security models to manage AI Threats:
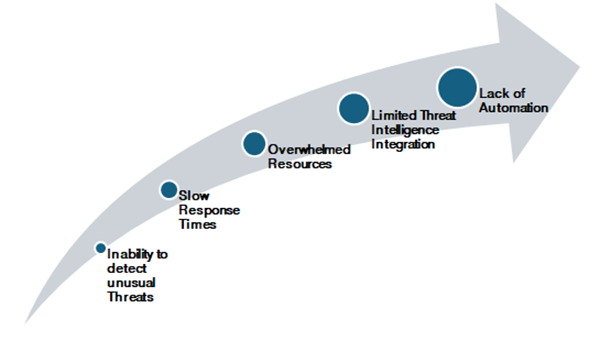
• Inability to detect unusual Threats: Traditional security models often rely on static signatures and predefined rules, making them ineffective against new and previously unseen AI-generated malware or attack techniques.
• Slow Response Times: Manual analysis and intervention are no match for the speed at which AI-powered attacks operate.
• Overwhelmed Resources: The sheer volume and complexity of AI-driven threats can quickly overwhelm traditional security teams and tools, resulting in missed alerts and insufficient coverage across networks and endpoints.
• Weakness in handling Social Engineering: Conventional defences are ill-equipped to recognise sophisticated social engineering tricks, such as deepfake-based phishing or voice impersonation, which can deceive even security-aware personnel.
• Limited Threat Intelligence Integration: Legacy tools often do not integrate with global threat intelligence platforms, missing out on real-time updates about emerging, AI-driven attack vectors.
• Reactive Rather Than Proactive Approaches: Traditional security models tend to respond to attacks after they occur, rather than predicting or preventing threats by analysing behavioural anomalies and unusual patterns.
• Lack of Automation: Without automation, traditional security operations centre (SOC) teams may become bogged down by repetitive tasks, unable to focus on strategizing against the most sophisticated threats.
Limitations of Traditional Security Tools
Traditional security solutions, such as signature-based antivirus software and static firewalls, were designed to detect known threats using predefined rules. While these tools are still essential for baseline protection, they struggle to keep pace with novel, AI-driven attacks that constantly evolve and mutate.
• Signature-based detection: Relies on known malware signatures, but AI attacks create new variants that evade detection.
• Rule-based firewalls: Static rules are easily bypassed by adaptive AI attack strategies.
• Manual monitoring: Human analysts struggle with the speed and scale of AI-driven threats.
In short, the dynamic and unpredictable nature of AI-powered threats exposes the limitations of conventional defences.
The Case for Next-Generation Cyber Security
To keep pace with AI-enabled hackers, organisations must augment their traditional defences with advanced, intelligent security solutions. These include:
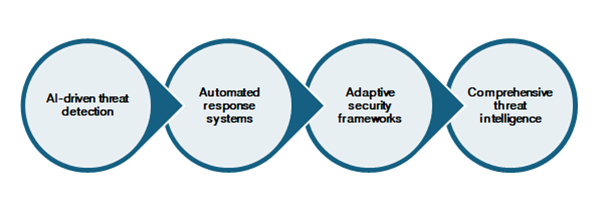
• AI-driven threat detection: Security platforms that use machine learning and behavioural analytics to identify anomalies and suspicious activities, even those not seen before.
• Automated response systems: Tools that can respond to threats in real time, containing breaches and neutralising attacks without human intervention.
• Adaptive security frameworks: Solutions that continuously learn and update their defence mechanisms, staying one step ahead of evolving threats.
• Comprehensive threat intelligence: Integrating global threat data and predictive analytics to anticipate and block emerging attack patterns.
By embracing these next-generation tools, organisations can level the playing field against AI-enabled adversaries.While AI is crucial for modern cyber defence, it is not a silver bullet. Skilled security professionals are needed to interpret AI-generated insights, make strategic decisions, and respond to complex incidents.The integration of AI by hackers has significantly transformed the cybersecurity landscape and it’s time for the Organisations to reshape their existing cybersecurity posture to handle AI threats. By continuously evolving our defences, we can strive to stay ahead in this dynamic digital arms race.
About the Author :

Ms. Kavitha Srinivasulu
CCISO | DPO| DTO| CISA | CRISC | CISM | CGEIT | PCSM | IAPP AIGP | ISO42001: LA
Program Director: Cybersecurity & Data Privacy
Tata Consultancy Services
Ms. Kavitha Srinivasulu is an Award winning Technology Leader.
Ms. Kavitha Srinivasulu is a Senior Cyber Risk and Resilience executive with over 22 years of global leadership experience advising Boards and Executive Committees across Financial Services, Healthcare, Retail, Technology, and regulated industries.
Ms. Kavitha Srinivasulu has delivered and led large-scale, regulator-driven cybersecurity, AI driven, PCI, and SOC transformations for Tier-1 banks, global healthcare organisations, and highly regulated enterprises operating across the UK, EU, USA, APAC, and ANZ.
Ms. Kavitha Srinivasulu is a trusted advisor to Boards, C-suite, regulators, and global enterprises, consistently delivering resilient, compliant, and scalable cyber operating models.
Ms. Kavitha Srinivasulu is an Advisory Member in National Cyber Defence Research Centre (NCDRC)
Ms. Kavitha Srinivasulu is a Board Member of Women in CyberSecurity (WiCyS) India
Ms. Kavitha Srinivasulu is an Executive Committee Member at CyberEdBoard Community
Ms. Kavitha Srinivasulu is an ambassador at ISAC
Ms. Kavitha Srinivasulu is Bestowed with the following Licenses & Certifications :
https://www.linkedin.com/in/ka
https://www.linkedin.com/in/ka
Ms. Kavitha Srinivasulu can be contacted at :
Disclaimer :
“The views and opinions expressed by Ms. Kavitha Srinivasulu in this article are solely her own and do not represent the views of her company or her customers.”
Also read Ms. Kavitha’s earlier article: