IoT Security – Mitigating the Risks of Connected Devices
Who would’ve thought a few years ago that someone could ruin your life because they hacked your fridge? It sounds ridiculous, but with the rise of the Internet of Things (IoT), this scenario is not so far-fetched. In fact, one notable incident occurred in 2014, when researchers demonstrated that a smart refrigerator could be hacked to send spam emails. The researchers were able to gain access to the fridge’s operating system and use it to send over 750,000 spam emails.
While the impact of this incident was not severe, it highlights the vulnerability of IoT devices and the potential consequences of a successful attack. If a hacker were able to gain access to a refrigerator or other IoT device connected to a home network, they could potentially gain access to sensitive information, such as credit card details, personal documents, and even video footage from security cameras.
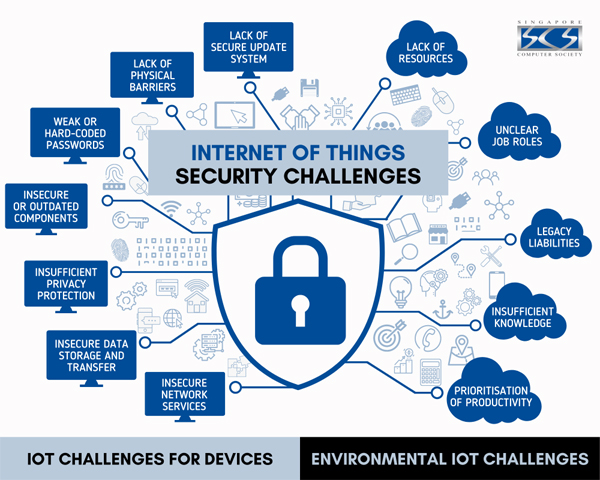
IoT devices are everywhere, from smart homes to industrial machinery, and they are designed to connect to the internet and share data. While the benefits of IoT are clear, the risks associated with these devices cannot be ignored. This is why it’s so important to prioritize IoT security and take steps to mitigate the risks associated with these devices. By following best practices, staying up to date with the latest security patches, and learning from real-world examples, we can help protect ourselves and our devices from potential cyberattacks.
Hackers can exploit weaknesses in IoT devices to gain access to networks, steal data, and cause damage to critical infrastructure. This has serious implications for both individuals and organizations, as the consequences of a successful attack can be catastrophic. In this article, we will discuss the key considerations for IoT security.
Authentication and Access Control

Strong authentication measures are critical to prevent unauthorized access to IoT devices and networks. This can include password policies, two-factor authentication, and biometric authentication. Access control measures should also be implemented to limit access to sensitive data and functions.
Best Practice: Implement strong authentication measures, such as password policies and two-factor authentication.
In 2016, the Mirai botnet attack targeted vulnerable IoT devices and used them to launch a DDoS attack on the DNS provider Dyn, causing widespread internet disruption for several hours. One of the ways Mirai was able to propagate was by exploiting weak default usernames and passwords.
To prevent such attacks, strong authentication measures should be put in place, such as password policies, two-factor authentication, and biometric authentication. Access control measures should also be implemented to limit access to sensitive data and functions.
Encryption

Data transmitted between IoT devices and networks should be encrypted to prevent interception and tampering. Encryption should also be used to protect data stored on IoT devices, as well as backups and archives.
Best Practice: Use encryption to protect data transmitted between IoT devices and networks, as well as data stored on IoT devices.
In 2019, security researchers discovered that the MiSafes smart baby monitor, which uses unencrypted communication, was vulnerable to hacking. Attackers could remotely access the monitor’s camera, speaker, and microphone, allowing them to spy on and communicate with children.
Encryption is essential to prevent interception and tampering of data transmitted between IoT devices and networks. Encryption should also be used to protect data stored on IoT devices, as well as backups and archives.
Software Updates

IoT devices should be regularly updated with the latest software patches and security fixes to address vulnerabilities. This is particularly important for devices that are connected to the internet, as they are more vulnerable to attack.
Best Practice: Regularly update IoT devices with the latest software patches and security fixes.
In 2017, the WannaCry ransomware attack infected hundreds of thousands of computers worldwide, including many IoT devices. The attack exploited a vulnerability in Windows operating systems that had already been patched by Microsoft months earlier.
This could have been prevented by regularly updating IoT devices with the latest software patches and security fixes to address vulnerabilities.
Physical Security

All IoT devices should be physically secured to prevent theft or tampering. This can include measures such as locks, alarms, and surveillance cameras.
Best Practice: Physically secure IoT devices to prevent theft or tampering.
In 2018, a couple in Milwaukee, Wisconsin in the USA had their smart home system hacked, causing their thermostat to be turned up to 90 degrees Fahrenheit. The incident led to a police response, and the couple was forced to reset their system to factory settings.
Physical security measures should be put in place to prevent theft or tampering of IoT devices. This can include measures such as locks, alarms, and surveillance cameras.
Monitoring and Analysis
IoT networks should be monitored and analyzed for signs of suspicious activity. This can include anomaly detection, behavior analysis, and threat intelligence feeds.
Best Practice: Monitor and analyze IoT networks for signs of suspicious activity.
In 2016, a Mirai botnet attack took down the internet in Liberia by targeting its only undersea fiber optic cable. The attack was detected by monitoring and analysis of network traffic, which allowed the local internet service provider to isolate and mitigate the attack.
Following this, the US Securities and Exchange Commission (SEC) issued a warning about the risks associated with IoT devices, citing the potential for attackers to manipulate market information or disrupt trading platforms. IoT networks should be monitored and analyzed for signs of suspicious activity. This can include anomaly detection, behavior analysis, and threat intelligence feeds.
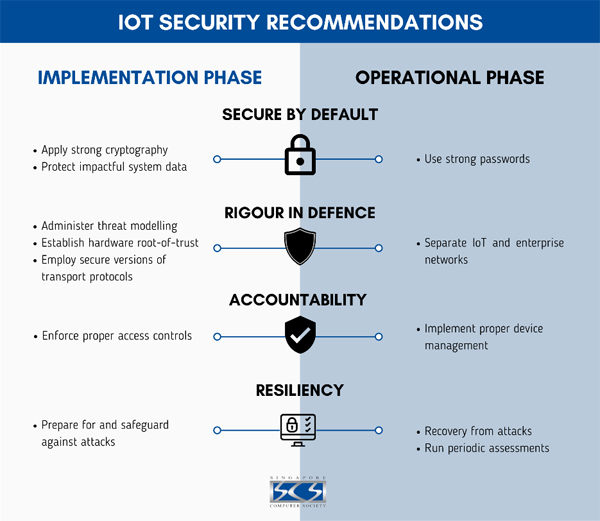
These highlight the importance of monitoring and analyzing IoT networks for signs of suspicious activity, such as anomaly detection, behavior analysis, and threat intelligence feeds.
In conclusion, let’s all remember that while IoT devices bring convenience to our lives, they also pose significant security risks. We don’t want to end up being the one whose fridge got hacked and food (or reputation) ruined! So, take the necessary steps to secure your devices, whether it’s updating software, changing passwords, or implementing access control measures. And let’s not forget about physical security too – maybe it’s time to invest in some locks and cameras for those smart home devices.
As technology advances, so do the methods and tools that hackers use to exploit vulnerabilities in our IoT devices. That’s why it’s crucial to stay informed and proactive in protecting our devices and networks. By learning from real-world incidents and applying best practices, we can ensure that the benefits of IoT are maximized while minimizing the risks.
At IDC technologies, we specialize in providing comprehensive security solutions for organizations of all sizes and industries, including those in the fisheries and farming sectors. Our team of experts stays up to date on the latest OT and IT security threats and trends, and we use that knowledge to help our clients stay ahead of potential threats and keep their operations running smoothly and to protect their devices and networks.
We offer a range of services to help organizations secure their IoT devices, from vulnerability assessments and penetration testing to ongoing monitoring and maintenance.
Whether you’re a small business or a large corporation, our team has the expertise and experience to help you secure your IoT devices and networks. Contact us today to learn more about our services and how we can help you stay protected in an increasingly connected world.
About the author :

Mr. Devarghya Debroy
Lead – Cyber Security Practice
IDC Digital
Mr. Devarghya Debroy has helped to create the organization’s first Information Security program.
Mr. Devarghya Debroy Responsibilities in IDC Digital include:
- Creating and Enforcing Cyber Security & Risk Management Policies for the worldwide organisation spanning 15 countries and documenting them
- Enforcing Governance and Risk Compliance Measures
- Applying Stringent Identity and Access Management along with Entitlement Management
- Monitoring and Triaging alerts
- Identify Security incidents and quickly mitigate them
- Build Corporate Security Playbooks
- Automate alerts, tasks, deployments, and reports
- Create and send advisory and educational content for organization-wide security awareness
- Perform real-world phishing simulations and develop interesting training to defend against it
- Harden infrastructure perimeter defense
Inculcate secure coding practices among inhouse developers by giving presentations and performing penetration tests - Build Business cases and open source solutions for Security technologies
- Building and leading a SOC Team
Mr. Devarghya Debroy is Bestowed with the following Licenses & Certifications :
https://www.linkedin.com/in/devarghya-debroy-b01152141/details/certifications/
About IDC Technologies, Inc. :
IDC Technologies Inc, established in year 2003, headquartered in Silicon Valley, California, USA with branch offices in Dallas, TEXAS, Irvine, CA & has international presence in Mexico, UAE, Canada, India (Noida, Hyderabad, Lucknow, Chennai, Bangalore, Pune, Coimbatore & Gurgaon). We provide effective business solutions in IT Consulting & Staff Augmentation, Project Management, Product Engineering and Business Process Outsourcing Services.
IDC provides consulting and IT services to clients globally – a partners to conceptualize and realize technology driven business transformation initiatives. With a world-class infrastructure and a global network, IDC offers a wide array of solutions for a range of key verticals and horizontals; starting from the strategy consulting right through to implementing IT solutions for clients.
We provide solutions for a dynamic environment where business and technology strategies converge. Our approach focuses on new ways of business combining IT innovation and adoption while also leveraging an organization’s current IT assets.
As a diverse end-to-end IT solutions provider, the company offers a range of expertise aimed at helping customers re-engineer and re-invent their businesses to compete successfully in an ever-changing marketplace. Our onsite and offshore development model allows us to leverage local competencies to offer global competitiveness to our clients ensuring high quality, on time delivery, at significantly reduced costs. We use a low-risk Model to accelerate schedules with a high degree of time and cost predictability.
To know more about IDC Digital offerings :

Mr. Deependra C
Regional Business Manager – IDC Digital
Phone: +91 98853 68407
E-mail : [email protected]
Web : www.idctechnologies.com/idcdigital/
IDC Technologies Inc. can be contacted at :
E-mail | Website | LinkedIn | FaceBook | Instagram | Twitter












