Cognitive Framework for Wildlife Monitoring and Management
A discussion of how IoT and AI can be used around the world to protect animal species as well as protect humans from unintended, but dangerous, animal interactions.
Wildlife Issues
Despite significant work to protect wildlife and manage national parks and forests, many incidents continue to occur every year, either causing loss to human beings or to wildlife.
While we are using Artificial Intelligence to solve complex problems such as predicting failures of complex equipment, performing natural language processing, making driver-less cars, and so on, applying technology to protect wildlife needs more work. Presented here is a non-evasive method and framework which effectively uses IoT enabled cognitive systems to make a drastic improvement in this domain.
Framework for the Monitoring and Management of Wildlife
The proposed framework is based on some of the proven behavioral attributes of different animals which can be further customized as we learn more about these animals. The framework consists of four stages which occur simultaneously to effectively monitor and manage wildlife movement:
- Detection: Detect movement patterns with thermal imaging.
- Identification: Identification of key entry and exit points of protected wildlife regions.
- Prevention: Preventing wildlife from exiting protected regions by the deployment of IoT-enabled devices.
- Control: Driving wildlife into safer regions such as a forest/protected area with the deployment of IoT-enabled devices.
 Detection : Detect Movement Patterns With Thermal Imaging
Detection : Detect Movement Patterns With Thermal Imaging
The area under surveillance will be divided into four quadrants – with smart cameras and IoT devices (motion and proximity sensing devices) installed in a way that they cover at least a quadrant. These will be used to detect movement across the monitored perimeter and techniques such as thermal imaging will detect animal movements.
A solar or battery powered LORA (long range) WAN network will be used to orchestrate and control the IoT devices and relay back the detection message or patterns.
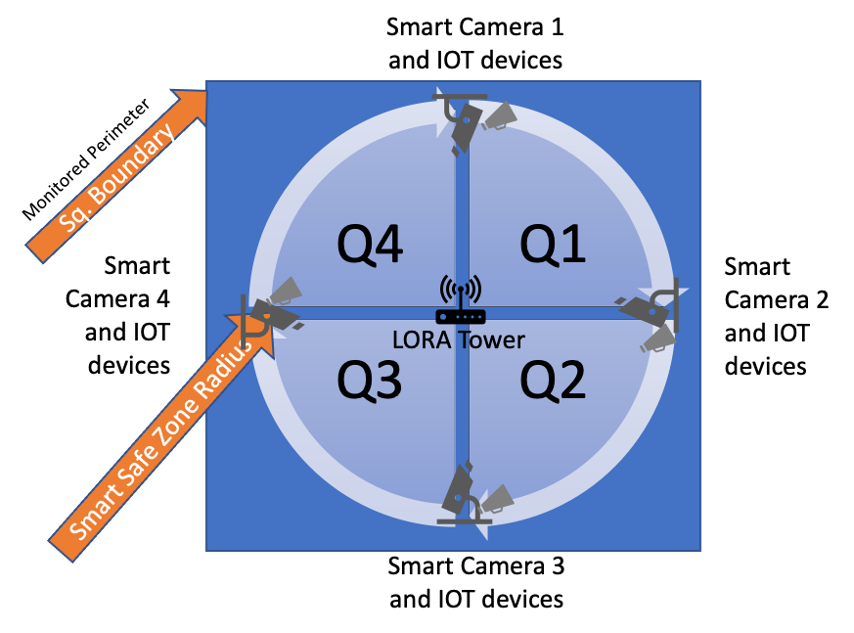
Illustrative example of detection using four quadrants and IoT devices
Identification: Identification of Key Entry and Exit Points of Protected Wildlife Regions
The proposed cognitive method will identify and establish a logical smart zone radius with key entry and exit points of protected wildlife regions using a combination of:
- Geo spatial data (terrain, contour vegetation, etc.).
- Weather data.
- Movement patterns detected using IoT devices and techniques such as thermal imaging.
The smart safe zone’s radius will iteratively self-adjust based on data insights from above mentioned parameters.
Prevention and Control: Identification of Key Entry and Exit Points of Protected Wildlife Regions
The proposed IoT-based cognitive framework will use a multi-layered learning model to:
- Dynamically adapt situation-aware tactics based on real-time factors (ex. animal conditions, aggression levels, etc.) and history, to trigger suitable action to guide the animal to safety.
- Combine spatial and temporal learning by co-relating features extracted from contextual sources (terrain, trajectory of movement, etc.), to assess time/frequency and direction of action.
- Recursively predict further reaction based on proximity and location trajectory within a bounded area by learning from previous actions, historical movement patterns, and surrounding factors, such as weather/mating season, presence of other animals, and so on.
- Iteratively adjust/re-adjust tactics by inferring temporal co-relations with parameters retrieved from sensors, cameras, etc., to dynamically classify/re-classify the situation when an animal moves within threshold proximities.
- Dynamically learn and enforce policies based on the nature of the animal and its history of interactions, by identifying physical/virtual zones using components like cameras, sensors/beacons, and entry/exit access data, in combination with historical access patterns and entity relationships (ex. leopard spotted in vicinity of sheep, avoids town center, etc.).
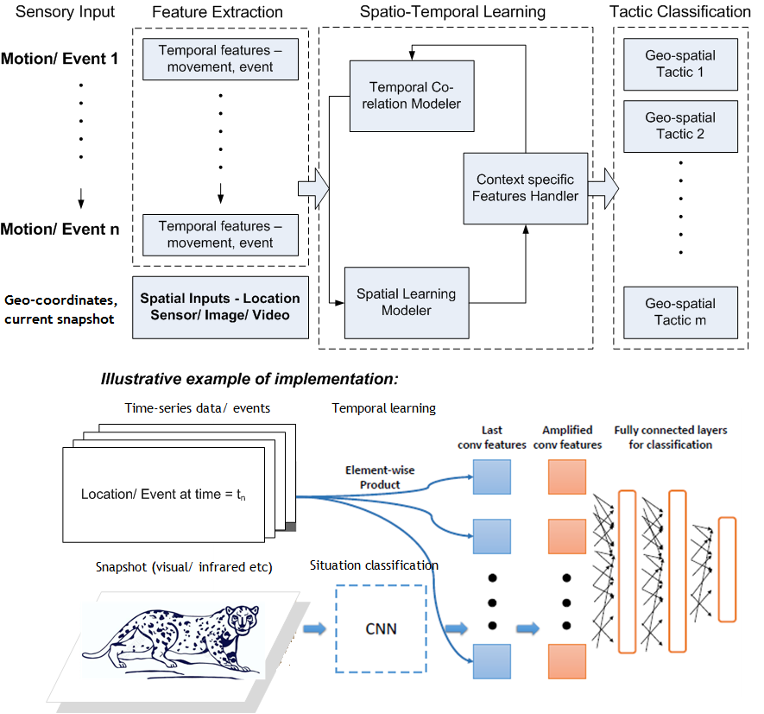
Example of a stacked deep learning model, such that coarse-grained features extracted from previous layers can be fed to subsequent layers to identify fine-grained patterns based on expert training and continuous feedback
Illustrative Case
Below is an example of how this framework will work and help prevent and control animal attacks.
Let us consider a Masai village in remote Kenya which is surrounded by predators and other types of animals and has no access to modern energy sources (e.g., electricity/gas).
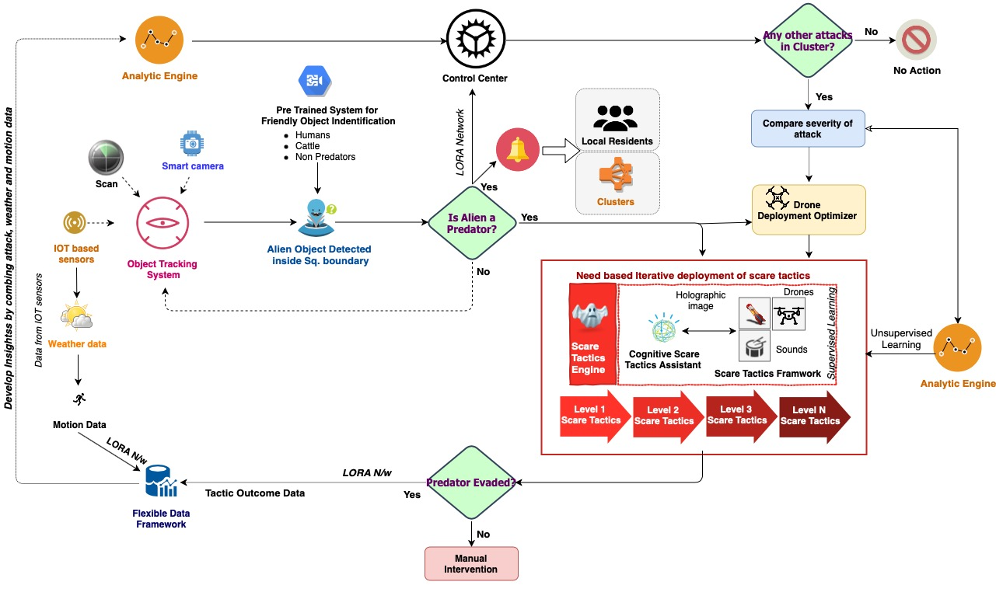
A group of animals is entering the square boundary or the monitored perimeter in middle of the night and gets detected as an alien object by a pre-trained system, a system which is a combination of smart cameras and IoT sensors that are constantly scanning the perimeter.
- If the pre-trained system detects a friendly object (e.g., livestock, villagers), then it does not initiate any action but still records the information via a control center. The information is used to enrich the analytics which are used to predict attacks.
- But if the system detects unfriendly objects (e.g., a lion, or a pride of lions), it will initiate three actions:
- It immediately alerts the control center using the solar or battery powered LORA network. The control center is a centralized mechanism which is established to protect a cluster of villages from animal attacks.
- It alerts the villagers through a pre-established solar or battery powered signaling mechanism which can produce either sounds familiar to villagers as danger signals or visual signals.
- Triggers the cognitive scare tactic assistant which uses a combination of supervised and unsupervised machine learning techniques to:
α. assess the severity of the attack using data from object detection systems, sensors, etc. installed in the village and/or clusters and in conjunction with the control center.
β. iteratively deploy scare tactics using a framework comprising of:
- pre-trained images that scare animals projected using techniques such as holographic imaging. In this particular case, a holographic image of a Masai group, fire, or another pride can be projected.
- pre-trained associated sounds that scare animals emitted alongside heat effects. In this particular case, the sounds of a Masai dance, a drum beat, and the crackling sound of wood along with fire, or a lion roar from another pride can be emitted along with heat effect to cause severe discomfort to predators.
- using a network of drones to induce external elements such as spray deterrent fluids or fire tranquilizers to temporarily immobilize animals. In this case, if the above two tactics fail to scare animals away from the safe radius zone, drones will be used to fire tranquilizers to temporarily immobilize lions. If the above two tactics succeed to scare way a lion pride, drones can be used to move them in a particular direction and track their further movement.
γ. self-learning from the event – iteratively improving the level of scare tactics based on an effectiveness quotient and improving the attack predictability analytics. Overall, the cognitive scare tactic assistant helps us to iteratively deploy appropriate levels of tactics which are used to (a) prevent the predator from crossing the safe zone radius (b) make the predator move in a favorable direction and to learn from those events.
4. The entire event is captured using a flexible data framework and is used to iteratively improve the effectiveness of the deployment of scare tactics and lessen human-animal conflict.
5. In a worst case scenario, if all deployed measures fail, the framework will signal for explicit human intervention via the control center.
The below diagram provides a visual representation of the above scenario:
Key Takeaways
Considering how quickly endangered species are disappearing from the face of earth and how humans continue to encroach on their habitats, there has never been a better time to exploit state of the art technology to accelerate wildlife conservation and to prevent loss of human lives because of unintended movements of animals. Our proposed non-evasive method and framework leverages the power of:
- inter-connected (IoT) devices to enable real-time wildlife movement detection across heterogenous networks and improve associated decision making.
- artificial intelligence to iteratively establish smart safe zones along with entry and exit points based on animal movements.
This tech-for-good method and the framework of leveraging IoT and cognitive technologies has the potential to dramatically improve the way people and animals can co-exist without causing harm or undesired fatalities.
About the Authors:

Mr. Rajeev Mittal,
Associate Partner with IBM Consulting
Rajeev Mittal has 22+ years of extensive experience with services, software development, development processes, client relationships, and project & people management.Led Transformation programs for client in Digital, Analytics, Cloud, Automation, Dev Ops, Agile development. He is also a Certified Professional Google Cloud Architect.
He is bestowed with the following Licenses & Certifications :
https://www.linkedin.com/in/mr
He can be Contacted at :
LinkedIn : mr
Email : [email protected]
Mobile : +91 9811 542076
Twitter : mrajeev74
 Mr. Pinaki Bhattacharya
Mr. Pinaki Bhattacharya
Delivery Project Executive at IBM
Pinaki Bhattacharya has 17 years of extensive experience in digital transformations, industry consulting, managing P&L, and people management. He has multiple technical disclosures published. He is passionate about education at grass root level and volunteers himself as an Educator at e-Vidyaloka.
He is a Strategic Advisor to Charity IT Association – CITA. He is also a Fund Raiser & Social Investor at Rang De
He is bestowed with the following Licenses & Certifications :
https://www.linkedin.com/in/pi
He can be Contacted at :
LinkedIn : pi
Twitter : Globetrott
 Mr. Harish Bharti
Mr. Harish Bharti
Distinguished Engineer and Master Inventor at IBM Consulting
![]()
Harish Bharati has wide experience in designing IT Solutions to Client Business Problems, using wide spectrum of Software Technologies. He is a key inventor for 34 File rated Patents on emerging technologies including Cloud, Cognitive Computing, API Modeling, Mobility Digital Integration
and Internet of Things.
Check his Google Scholar profile :
https://scholar.google.co.in/c
He is bestowed with the following Licenses & Certifications :
https://www.linkedin.com/in/ha
https://www.credly.com/users/h
He can be Contacted at :
LinkedIn : ha
Mr. Dinesh Wadekar
Senior Software Developer at IBM
Dinesh Wadekar has over Fifteen years of IT industry experience with wide range of skill sets, roles in various accounts in IBM. He has 4 Intellectual Capital/ Patents are issued by US Patent Office (USPTO) & 19 research disclosures Published on IP.com. He has got an honor of IBM Services Senior Inventor for the ability to capture business and technical innovation through patenting.He has in depth understanding of the principles and best practices of software configuration management (SCM) in Agile, Scrum and Waterfall methodologies.
He is working as a Tableau Developer and Analyst in Enterprise Environments with Tableau 9, 10, 2019, 2020. His expertise is in designing and developing dashboards using Tableau Desktop and Tableau Server as well as designing, developing, and publishing visually rich and intuitively interactive Tableau workbooks. He has knowledge on Devops Tools – Git, Maven, Jenkins, Ansible, Sonarqube, Docker.
He is bestowed with the following Licenses & Certifications :
https://www.linkedin.com/in/di
He has received following Honors & Awards :
https://www.linkedin.com/in/di
He can be Contacted at :
LinkedIn : di










