Cyber Risk, Protection and Safety in 2023
Cyber risk refers to the potential for loss or damage to an organization’s information technology systems, data, or reputation as a result of a cyber attack or other malicious activity. Cyber risk can arise from a variety of sources, including external hackers, insider threats, and unintentional user errors.
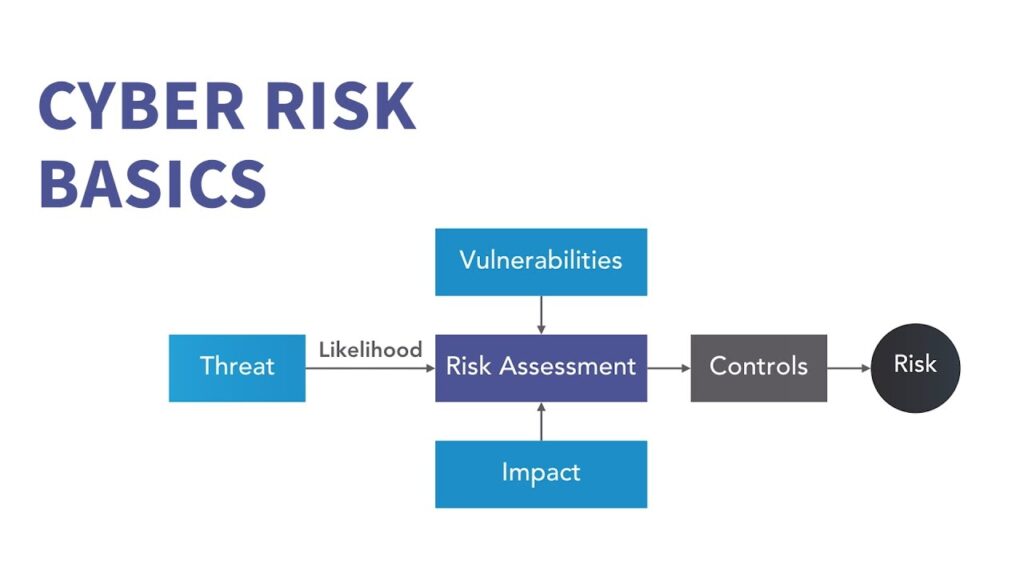
Cyber risk is no longer a technology problem – it has become a constantly evolving systemic risk for organizations and societies that must be actively managed. With dramatic increases in remote work, supply chain interconnectivity, digitization pressures, and critical infrastructure vulnerabilities, organizations are more exposed than ever. To thrive, they must move beyond protection to resilience.
Many organizations look at cybersecurity as an operational or technology problem and are spending more every year on cybersecurity solutions. Yet the scale, frequency, and economic impact of cyber events – whether ransomware, supply chain attacks, or business interruptions – continues to grow.
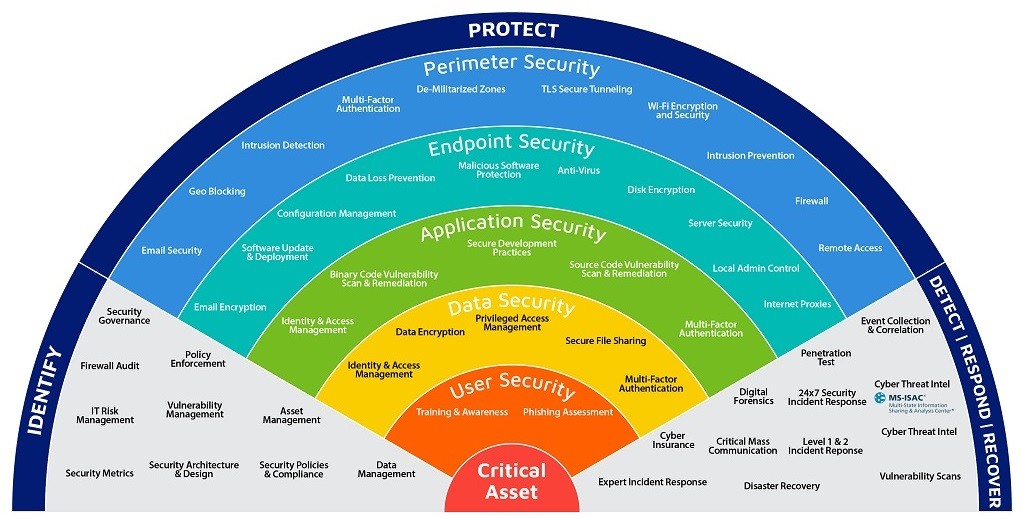
We are trusted risk advisors, building and delivering best-in-class capabilities and solutions to help our clients understand, measure, and manage their cyber risk. We enable better strategic decision-making around your cyber risk through our advisory services and technologies for insurance, incident management, risk intelligence, and resilience optimization.
Ensuring cyber safety involves implementing measures to prevent and mitigate the effects of cyber attacks and other cyber threats. This can include implementing strong passwords and multi-factor authentication, keeping software and systems up-to-date with the latest security patches, encrypting sensitive data, and monitoring systems for suspicious activity.
In addition to technical measures, cyber safety also involves educating users about safe computing practices and raising awareness about the potential risks of cyber threats. This can include training users on how to recognize phishing emails and other social engineering tactics, as well as encouraging them to report any suspicious activity to IT or security personnel.
Ultimately, maintaining cyber safety requires a comprehensive approach that involves both technical and non-technical measures, as well as ongoing vigilance and proactive risk management.
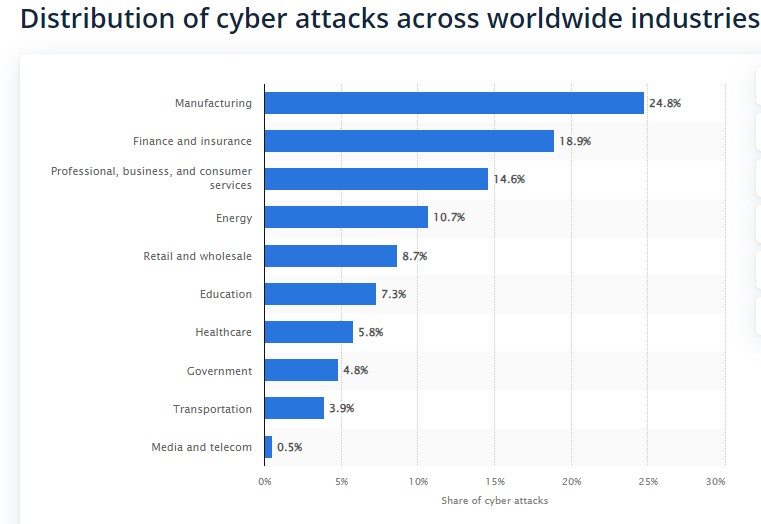
We can help you assess and quantify your cyber risk, prepare for and respond to cyberattacks, transfer your risk, and build lasting risk management and resilience.
Here are a few examples of effective user training for recognizing phishing emails:
1. Simulated phishing exercises: One effective way to train users to recognize phishing emails is to conduct simulated phishing exercises. These exercises involve sending mock phishing emails to employees and monitoring their responses. If an employee falls for a mock phishing email, they can be provided with immediate feedback and guidance on how to identify and avoid similar attacks in the future.
2. Interactive training modules: Interactive training modules can be an engaging and effective way to educate employees about phishing. These modules can include interactive quizzes, videos, and other multimedia content that teach employees how to identify and avoid phishing emails. Some examples of interactive training modules include PhishMe and KnowBe4.
3. Real-life examples: Another effective way to train employees to recognize phishing emails is to provide real-life examples of successful phishing attacks. These examples can be used to illustrate common phishing tactics and help employees understand the consequences of falling for a phishing email. This can also help to make the training more relatable and relevant to employees.
4. Ongoing training: Finally, it’s important to ensure that phishing training is an ongoing process rather than a one-time event. Regularly reminding employees about the risks of phishing and providing them with updated information about new threats can help to keep phishing awareness top of mind and reduce the likelihood of successful attacks.
#cyberattack, #cyberprotection, #cyberrisk, #security, #tech
About the author :
Mr. Vinod Gokakakar
MD & CEO,
EBC TECH SERV PVT LTD (ETSPL)
Vinod Gokakakar is a seasoned IT professional with over 21 years of diverse experience in the technology industry. Throughout his career, Vinod has worked with a wide range of sectors, from small businesses to multinational corporations, gaining invaluable insights into various technological verticals.
In 2017, leveraging his extensive expertise and recognizing the growing importance of cybersecurity for businesses, Vinod took a bold step and established his own company. Focused on serving small and medium-sized enterprises (SMEs), his company aimed to provide comprehensive cybersecurity solutions to protect these businesses from emerging
threats in the digital landscape. Vinod‘s commitment to safeguarding the digital assets of SMEs earned him a reputation as a trusted advisor in the cybersecurity domain.
Building on his success and driven by a passion for addressing complex challenges in the digital realm, Vinod expanded his entrepreneurial ventures further. In 2017, he founded ETSPL and in 2022 he founded another company BEPPL (Business Entente Powers Pvt Ltd) dedicated to providing a comprehensive suite of services encompassing cybersecurity, legal advisory, copyrights, intellectual property rights (IPR), online dispute resolutions, and more. This innovative venture positioned Vinod as a pioneer in offering integrated solutions that bridge the gap between technology and legal compliance.
Vinod‘s visionary leadership and multidisciplinary approach have positioned his companies as leaders in the cybersecurity and legal services sectors in India. His ability to anticipate emerging trends, coupled with a deep understanding of both technology and legal frameworks, has enabled him to offer holistic solutions tailored to the evolving needs of his clients.
With a track record of success and a commitment to excellence, Vinod Gokakakar continues to make significant contributions to the advancement of cybersecurity and legal services, empowering businesses to navigate the complexities of the digital age with confidence and resilience.
Mr. Vinod Gokakakar is Bestowed with the following Licenses & Certifications :
https://www.linkedin.com/in/vinodgokakakar/details/certifications/
Mr. Vinod Gokakakar is Accorded with the following Honors & Awards :
https://www.linkedin.com/in/vinodgokakakar/details/honors/
Mr. Vinod Gokakakar can be contacted at :
About EBC TECH SERV PVT LTD:
We are expertise in the Cyber Security & IT services. We work on simple principle Discussion, Initiatives, Testing & Execution.
Join hands with us to accelerate your business success!
EBC TECH SERV PVT LTD can be contacted at:
FaceBook | LinkedIn | YouTube | Website | E-mail
About Ententepower :
At BEPPL (Business Entente Powers Pvt Ltd), Our cyber security services encompass a wide range of solutions, including threat intelligence, vulnerability assessments, penetration testing, incident response, and security awareness training.
Ententepower can be contacted at :
Also read Mr. Vinod Gokakakar’s earlier article :












